BYOC is offered to enterprise customers only.
If you’re interested in BYOC offering, please book a call with our team here or contact us at enterprise@e2b.dev.
Architecture
Sandbox templates, snapshots, and runtime logs are stored within the customer’s BYOC VPC. Anonymized system metrics such as cluster memory and cpu are sent to the E2B Cloud for observability and cluster management purposes. All potentially sensitive traffic, such as sandbox template build source files, sandbox traffic, and logs, is transmitted directly from the client to the customer’s BYOC VPC without ever touching the E2B Cloud infrastructure.Glossary
- BYOC VPC: The customer’s Virtual Private Network where the E2B sandboxes are deployed. For example your AWS account.
- E2B Cloud: The managed service that provides the E2B platform, observability and cluster management.
- OAuth Provider: Customer-managed service that provides user and E2B Cloud with access to the cluster.
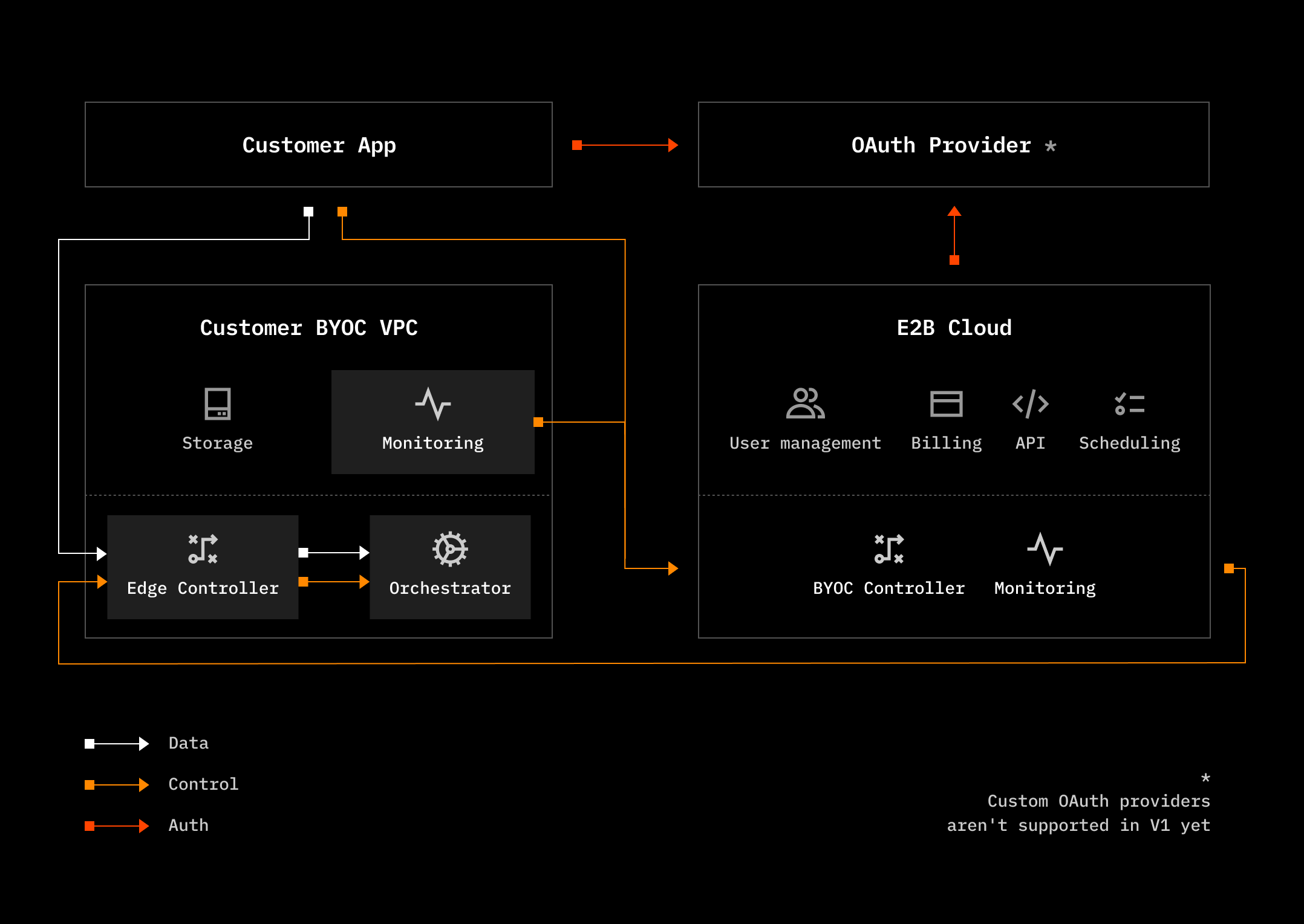
BYOC cluster components
- Orchestrator: Represents a node that is responsible for managing sandboxes and their lifecycle. Optionally, it can also run the template builder component.
- Edge Controller: Routes traffic to sandboxes, exposes API for cluster management, and gRPC proxy used by E2B control plane to communicate with orchestrators.
- Monitoring: Collector that receives sandbox and build logs and system metrics from orchestrators and edge controllers. Only anonymized metrics are sent to the E2B Cloud for observability purposes.
- Storage: Persistent storage for sandbox templates, snapshots, and runtime logs. Image container repository for template images.
Onboarding
Customers can initiate the onboarding process by reaching out to us. Customers need to have a dedicated AWS account and know the region they will use. After that, we will receive the IAM role needed for managing account resources. For AWS account quota limits may need to be increased. Terraform configuration and machine images will be used for provisioning BYOC cluster. When provisioning is done and running, we will create a new team under your E2B account that can be used by SDK/CLI the same way as it is hosted on E2B Cloud.FAQ
How is cluster monitored?
How is cluster monitored?
Cluster is forwarding anonymized metrics such as machine cpu/memory usage to E2B Control plane for advanced observability and alerting.
The whole observability stack is anonymized and does not contain any sensitive information.
Can cluster automatically scale?
Can cluster automatically scale?
A cluster can be scaled horizontally by adding more orchestrators and edge controllers.
The autoscaler is currently in V1 not capable of automatically scale orchestrator nodes that are needed for sandbox spawning.
This feature is coming in the next versions.
Are sandboxes accessible only from a customer’s private network?
Are sandboxes accessible only from a customer’s private network?
Yes. Load balancer that is handling all requests coming to sandbox can be configured as internal and VPC peering
with additional customer’s VPC can be configured so sandbox traffic can stay in the private network.
How control plane secure communication is ensured?
How control plane secure communication is ensured?
Data sent between the E2B Cloud and your BYOC VPC is encrypted using TLS.VPC peering can be established to allow direct communication between the E2B Cloud and your BYOC VPC.
When using VPC peering, the load balancer can be configured as private without a public IP address.